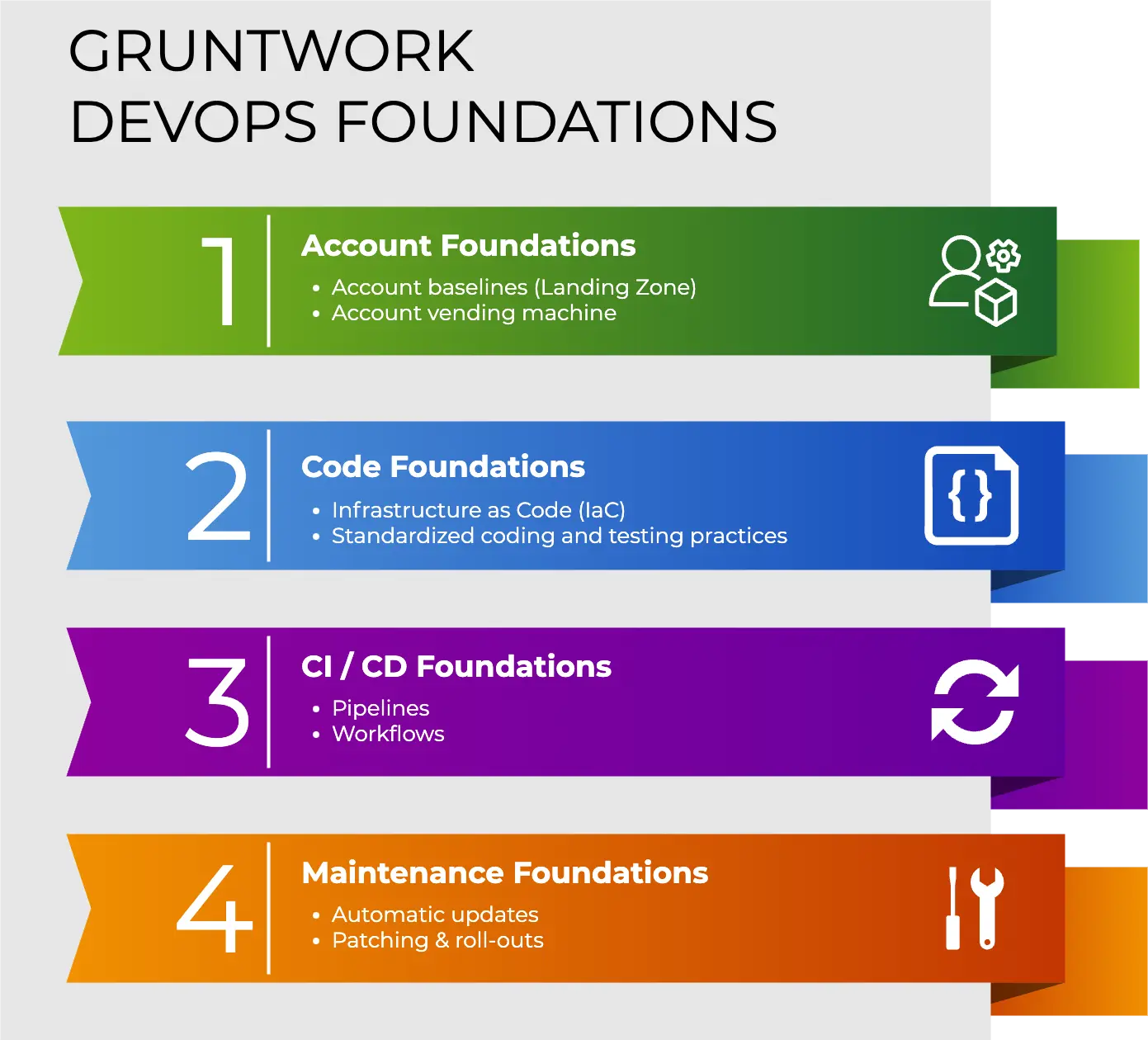
CIS Benchmarks are objective, consensus-driven configuration guidelines developed by security experts to help organizations improve their security posture. The CIS AWS Foundations Benchmark is a set of configuration best practices for establishing a secure foundation for running workloads on AWS. In September, 2020, version 1.3.0 of the benchmark was released, introducing a number of new security controls and recommendations. In this blog post, I’ll walk you through some background on the AWS Foundations Benchmark and what new requirements were added in version 1.3.0. Also, for Gruntwork Compliance customers, I’m happy to announce that we’ve updated all our modules to be compatible with version 1.3.0, so I’ll also walk you through how to update your code to pull in these changes to make all your infrastructure compatible with version 1.3.0 as well.
- AWS Foundations Benchmark Basics
- What changed in version 1.3.0
- How to update your infrastructure to be compatible with version 1.3.0
AWS Foundations Benchmark Basics
The CIS AWS Foundations Benchmark is a set of configuration best practices for hardening AWS accounts to establish a secure foundation for running workloads on AWS. It also provides ongoing monitoring to ensure that the account remains secure. The Benchmark is organized into the following sections:
- Identity and Access Management
- Storage
- Logging
- Monitoring
- Networking
There are multiple recommendations within each section. For example, the Identity and Access Management section includes 22 recommendations, such as how to configure your password policy, how to use IAM groups and IAM roles, and how to configure multi-factor authentication (MFA) devices. Similarly, the Logging section includes 11 recommendations related to logging, monitoring, and auditing using tools such as AWS CloudTrail, AWS Config, and VPC Flow Logs.
In all, there are over 50 recommendations to implement: see How to achieve compliance with the CIS AWS Foundations Benchmark for all the gory details. Configuring this all from scratch can take a significant amount of time, so a few years ago, we introduced the Gruntwork Compliance offering, which gets you access to a collection of reusable infrastructure code, plus an end-to-end Reference Architecture for AWS, both of which are fully compliant with the CIS AWS Foundations Benchmark out of the box.
What changed in version 1.3.0
Version 1.3.0 of the CIS AWS Foundations Benchmark was released in September of 2020 (you can download the benchmark from the CIS website).**** Below are the new recommendations introduced in version 1.3.0 of the Benchmark. You can think of these as a “diff” between versions 1.2.0 and 1.3.0:
- [1.19] Ensure that all the expired SSL/TLS certificates stored in AWS IAM are removed:**** All expired SSL/TLS certificates stored in AWS IAM should be automatically removed. This reduces the risk that an invalid certificate will be deployed accidentally to a resource such as AWS Elastic Load Balancer (ELB), which can damage the credibility of the application/website behind the ELB. As a best practice, it is recommended to delete expired certificates on a regular basis: e.g., run a Lambda function on a cron job that finds and deletes all expired certs.
- [1.20] Ensure that S3 Buckets are configured with ‘Block public access (bucket settings)’: All S3 buckets should have a setting enabled that explicitly blocks public access. This ensures that you don’t accidentally expose the potentially sensitive contents of those buckets to the outside world.
- [1.21] Ensure that the IAM Access analyzer is enabled: The new AWS IAM Access Analyzer service should be enabled across all active regions in a given AWS account or organization. This service will examine the trust policies and access to a variety of AWS services, including S3 buckets, IAM roles, KMS keys, and so on.
- [2.1.1] Ensure all S3 buckets employ encryption-at-rest: All S3 buckets should encrypt their contents by default when writing them to disk. This ensures all your S3 data is encrypted at rest.
- [2.1.2] Ensure S3 Bucket Policy allows HTTPS requests: All S3 buckets should enforce a policy that only allows them to be accessed over HTTPS. This ensures all your S3 data is encrypted in transit.
- [2.2.1] Ensure EBS volume encryption is enabled: All EBS volumes should enable encryption by default. This ensures all the data on your EC2 instances is encrypted at rest.
- [3.10] Ensure that object-level logging for write events is enabled for (CloudTrail) S3 bucket: All S3 write operations at the object-level—that is each write to an S3 bucket (
PutObject)—should be logged in CloudTrail. - [3.11] Ensure that object-level logging for reading events is enabled for (CloudTrail) S3 bucket: All S3 read operations at the object-level — that is each write to an S3 bucket (
GetObject)—should be logged in CloudTrail. - [4.15] Ensure a log metric filter and alarm exists for AWS Organizations changes: Create metric filters from log events related to any changes to your AWS Organization, and configure alarms around these metrics. This can help notify you of unexpected changes to your AWS Organization.
- [5.1] Ensure no network ACLs allow ingress from 0.0.0.0/0 to remote server administration ports: Configure Network ACLs (NACLs) that, by default, block all access to server administration ports (i.e., SSH and RDP ports). Then, allow access to those administration ports only from a specific subset of CIDR blocks (but NOT
0.0.0.0/0).
For more details on these new requirements, and all other AWS Foundations Benchmark requirements, check out How to achieve compliance with the CIS AWS Foundations Benchmark.
How to update your infrastructure to be compatible with version 1.3.0
A key part of the Gruntwork Compliance offering is that we provide commercial support and maintenance for the code, including incorporating the necessary updates whenever a new version of the AWS Foundations Benchmark is released. We have finished updating all of our code to meet the requirements of version 1.3.0 of the benchmark, so you now update your code to meet those requirements too!
For the most part, this solely requires updating the versions of the Gruntwork IaC Library that you were using. For example, if you were using the Gruntwork vpc-app module:
module "vpc" {
source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-app?ref=v0.12.0"
vpc_name = "example"
cidr_block = "10.0.0.0/16"
num_nat_gateways = 3
# ... other params ...
}
Then to be compatible with CIS version 1.3.0, you’ll need to update to version v0.13.0 of the vpc-app module, which now takes into account the new 1.20, 2.1.1, and 2.1.2 recommendations from the benchmark:
module "vpc" {
# Bump the ref param to v0.13.0!
source = "git::git@github.com:gruntwork-io/terraform-aws-vpc.git//modules/vpc-app?ref=v0.13.0"
vpc_name = "example"
cidr_block = "10.0.0.0/16"
num_nat_gateways = 3
# ... other params ...
}
In some cases, you’ll also need to deploy a new module. For example, to meet the new recommendation 5.1, you will need to deploy our new vpc-app-network-acls module:
module "vpc_app_network_acls" {
source = "git::git@github.com:gruntwork-io/terraform-aws-cis-service-catalog.git//modules/vpc-app-network-acls?ref=v0.10.0"
# Set params required by recommendation 5.1
allow_administrative_remote_access_cidrs_public_subnets = {
berlin_office = "1.2.3.4/32"
ny_office = "6.7.8.9/32"
}
# ... other params ...
}
To capture all the details, we’ve created a dedicated How to update to CIS AWS Foundations Benchmark v1.3.0 guide, which includes a version compatibility table to help you upgrade your existing modules to the new versions, and instructions on how to deploy the new modules required by 1.3.0.
Try it out!
If you’re upgrading from version 1.2.0 of the benchmark to version 1.3.0, follow our step-by-step upgrade guide; if you’re starting from scratch, check out our end-to-end How to achieve compliance with the CIS AWS Foundations Benchmark guide instead. Either way, let us know how it works for you! And if you have any questions, don’t hesitate to contact us.



- No-nonsense DevOps insights
- Expert guidance
- Latest trends on IaC, automation, and DevOps
- Real-world best practices